Topicus KeyHub, SSO, Access Management
We are pleased to announce the 9.1 release of Topicus KeyHub. This release fixes a security issue, brings several enhancements and addresses issues found in previous versions. It is recommended to update your KeyHub deployment.
Managing your applications and linked systems
TKH-493 TKH-494 TKH-585 Group managers can now manage the applications and linked systems for their groups. A group manager can decide the required security level for SSO or activation on the dashboard. KeyHub administrators no longer have access to secrets for OAuth applications unless explicitly shared by the group manager. The client identifier and secret can now be directly copied to the clipboard using a button. For linked systems, usage of a rotating password can be demanded for activation. All these settings can be found on the management page for 'My groups'. Click on an application or linked system and choose 'Details'.
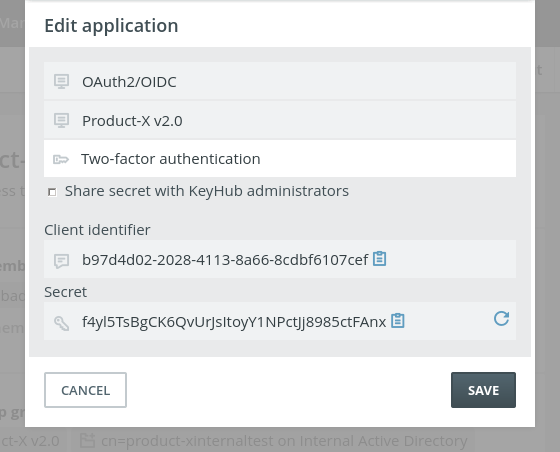
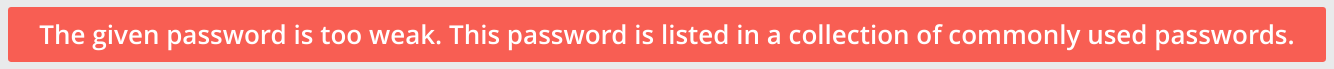
Ban weak passwords
TKH-574 Weak passwords are a major concern when it comes to securing accounts. Easy to guess passwords such as Password12345 or 987654321qwerty meet most length and/or complexity requirements but should still be avoided. KeyHub now bans over 450k commonly used passwords. Users with a banned password will be required to change their password on their next login.
Password expiry in the directory
TKH-301 When a user's password has expired in the directory, KeyHub will now guide the user through the password wizard and force the user to change his/her password.
Small improvements
The following smaller improvements and bugfixes were made:
TKH-548TKH-549TKH-618Code coverage from tests was increased substantially.TKH-567Improved applications overview under account when empty.TKH-589Improved error handling for AD provisioning.TKH-620Added support for English names for deployment configurations.TKH-621Fixed a race condition in session initialization that could trigger an error.TKH-622Increased timeout for 2FA via the app to 30 minutes.TKH-623Fixed an error with removing a former KeyHub Administrator account.TKH-624Fixed an error with activating a group which was deleted.TKH-625Fixed an error with reloading some pages after a session timeout.TKH-626Users are no longer blocked in the password wizard after entering an invalid password for the vaults.TKH-631Groups are now always deactivated when the timer expires.

