Topicus KeyHub 15.0
We are pleased to announce Topicus KeyHub 15.0. This release brings several enhancements to the vaults, notifications, the command line interface and account provisioning. As usual, a number of smaller improvements have been made and several issues have been fixed.
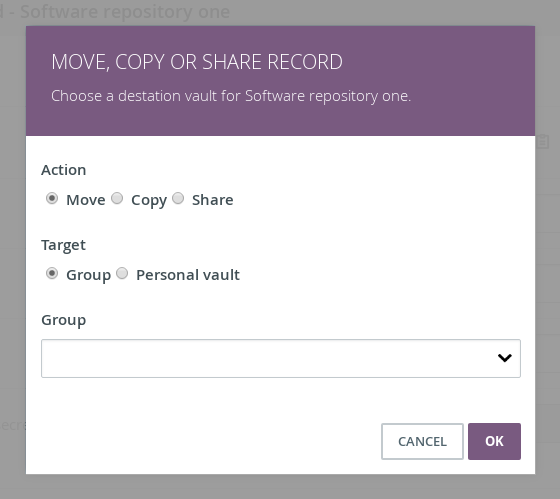
Sharing, copying and moving vault records
TKH-1029 TKH-1194 TKH-1244 TKH-1245 TKH-1246 TKH-1248 A whole new set of features has been added to the Topicus KeyHub vaults. You can now move, copy or even share a record to or with any other vault. A shared record will be read-only to the receiving vault and reflect all changes in the original record. Access to the target vault is not required. This allows you to share passwords with colleagues or transfer certificates to a group without requesting access to the vault. These features are accessible for group managers and your personal vault.
Notifications
TKH-1104 TKH-1161 TKH-1239 Never miss out on important notifications. Topicus KeyHub now checks for new notifications on a daily basis and sends you a digest of the notifications on your dashboard. This now also includes the certificate used by the IdP to sign OAuth tokens and SAML assertions. In addition, the appliance manager will notify the administrator if an update failed and caused a rollback.
Command line interface
TKH-1269 TKH-1270 TKH-1292 The command line interface now gives access to your rotating password. The new provisioning command group will be extended in a future version with dynamic provisioning support, allowing you to enable and disable groups directly from the command line. The zip file for the command line interface now also contains a Powershell and CMD wrapper for Windows.
Last but not least, an experimental native build for Linux was added. This native version runs much faster (keyhub status runs in just over 10ms rather than over half a second for the Java version) and does not require a full JDK installed. Unfortunately, due to limitations of the GraalVM native image compiler, it still requires a few shared object files from the JVM to run. Hopefully this will be fixed in a future version of GraalVM.
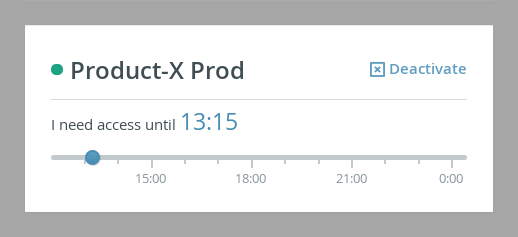
Account provisioning end time
TKH-771 TKH-842 Topicus KeyHub now remembers the duration of the previous activation of a group. For example, when you activate a group in the morning and set the end time to 18:00, Topicus KeyHub will automatically select 18:00 the next morning (based on the same duration). We would like to receive feedback on this feature, to see if this change is to the liking of our users.
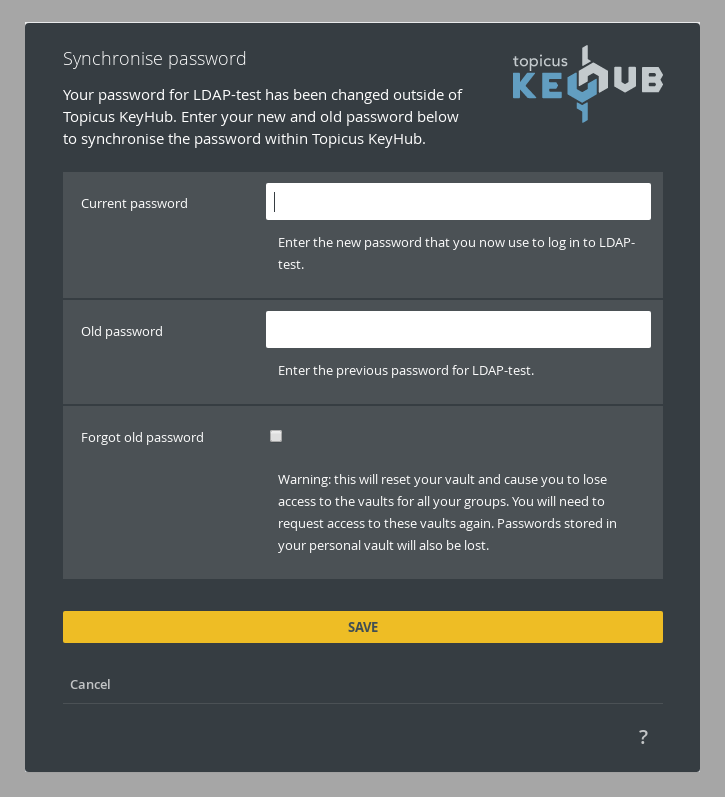
Password synchronization
TKH-1252 When you choose to synchronize your directory password with Topicus KeyHub, but change your password outside Topicus KeyHub, you are now prompted to re-synchronize your password. Previously Topicus KeyHub would silently disable synchronization resulting in a confusing situation. The re-synchronization requires your old and new password to re-encrypt your vault.
Small improvements
The following smaller improvements and bug fixes were made:
TKH-562TKH-853It is now possible to specify a fail over host for a linked LDAP or Active Directory.TKH-1243A user interface issue was fixed when setting a ssh public key for the backup user.TKH-1247It is no longer possible to setup an authorizing group for new groups.TKH-1249The RESTful API no longer gives all details for all accounts when querying for accounts.TKH-1253It is now possible to upload encrypted private keys and specify the password.TKH-1254Topicus KeyHub is now updated before system updates are installed, giving use the possibility to fix issues caused by system updates.TKH-1255It is now possible to provision the same linked system more than once as long as a different username prefix is specified.TKH-1256KeyHub administrators can now be removed via My Groups.TKH-1257Inactive accounts are now handled correctly with source directory provisioning, removing all provisioned groups.TKH-1258Resetting 2FA now correctly sends the reset push message to a connected device.TKH-1259The application server has been upgraded to WildFly 18.0.1.TKH-1260Very large attribute evaluation scripts no longer cause an error.TKH-1261Installing many system updates could cause a socket timeout exception, causing the update to fail.TKH-1263The Save and Test buttons on a linked system are no longer displayed when the user does not have permission to modify the linked system.TKH-1264The delivered virtual appliance contained traces of Topicus network configuration, these are now removed.TKH-1265The SaltStack reconfiguration no longer fails when no internet connection is available.TKH-1266When an error occurs when configuring the network on via the terminal, the interface now pauses to allow the user to read the error.TKH-1267It is now possible to change the DNS configuration without restarting all docker containers.TKH-1268Under some circumstances the installation could fail when using a self signed certificate.TKH-1271An error was fixed when performing re-authentication via the browser extension when a traditional TOTP app was used.TKH-1272The vaults page now supports more than 100 groups.TKH-1274All auto complete input fields are replaced by select2 components.TKH-1278An older database migration could have caused a misconfiguration of certificates, causing errors when removing a linked system.TKH-1279Restoring a backup was terminated prematurely, causing part of the database schema not to be restored. Backup restore was fixed and incomplete database schema's are repaired.TKH-1280Longer running updates could cause a timeout. This timeout has been increased.TKH-1281The RESTful backend now fully supports CORS.TKH-1283The password configuration wizards were missing the option to setup a rotating password for internal accounts in some cases.TKH-1285Using the breaking glass system to have two KeyHub administrators add a user to a group now gives access to the vault if possible.TKH-1286The name of the vault record for the installation password was changed to better reflect its origin.TKH-1288TOTP codes in the vault were missing leading zero's.TKH-1289Audit records for changes in group memberships now show the user making the change.TKH-1291An error was fixed when aborting the registration while configuring the password.TKH-1318Fixed a regression with the DNS configuration during install or when using DHCP. Patched in 15.0-1.

